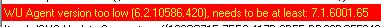
After some digging on the system, the installer can be found on the SCCM server or other sources could be another computer with the console installed and has been updated.
The directory where the files are found: "C:\Program Files (x86)\ConfigMgr10\AdminconsoleSetup"

In the directory, you'll find some GUID named folders. They will contain the "Adminconsole.msi" or the Console Update.
Depending on which source you get it from, you may have more than one folder containing the "Adminconsole.msi". Install using the newest created date.
After installing the console, run the latest console update from searching the same directory to avoid the console from prompting to update on first launch.